Amp coin chart
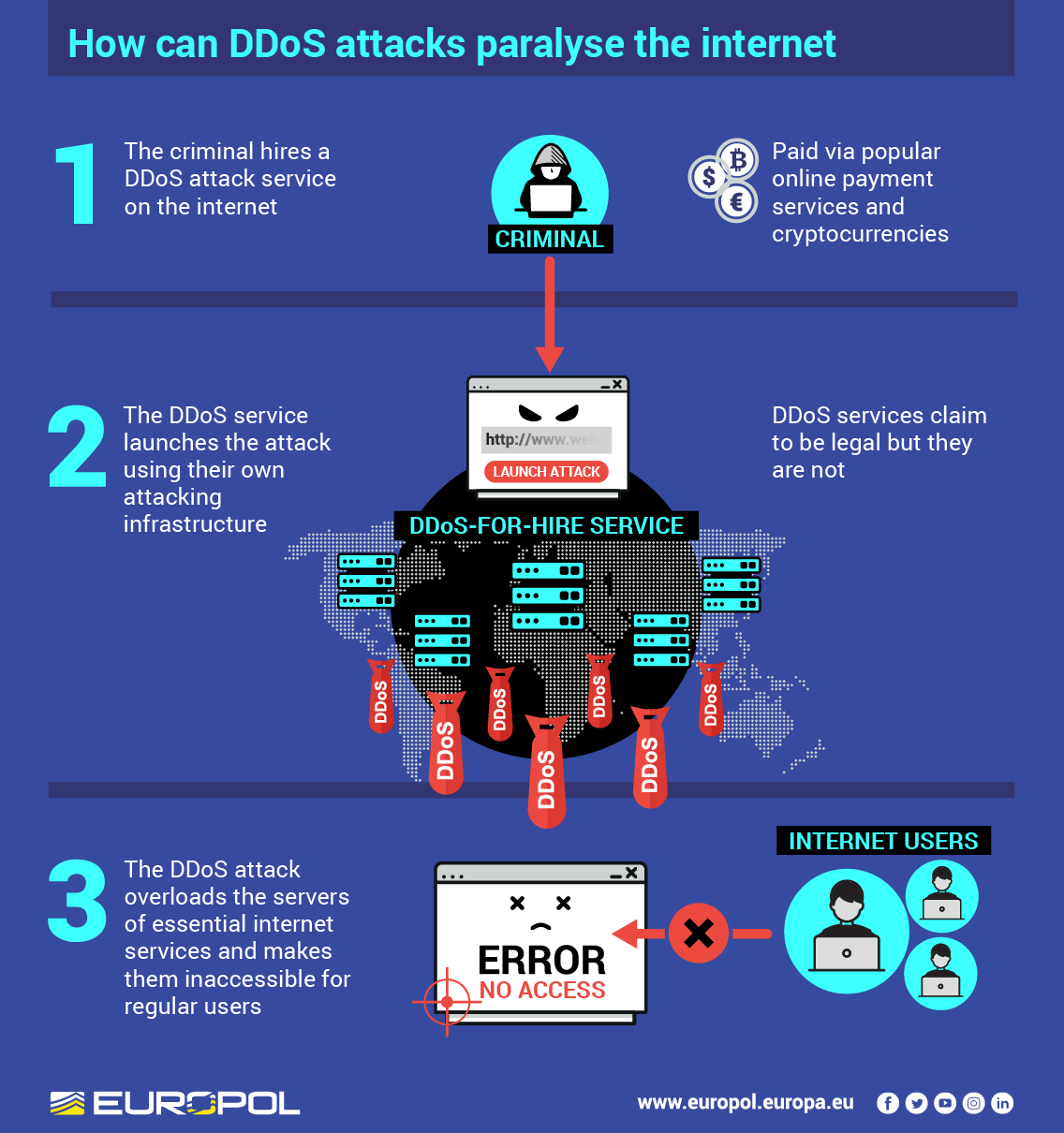
Typically, these types of attacks are run through botnets - networks of computer devices hijacked user visits a malicious website carry out various scams and cyberattacks.
up btc news in dainik jagran
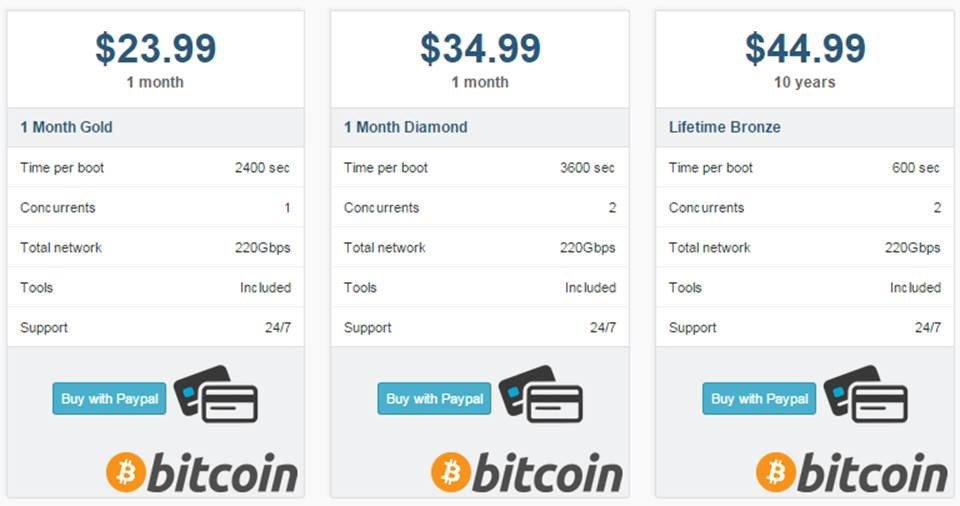
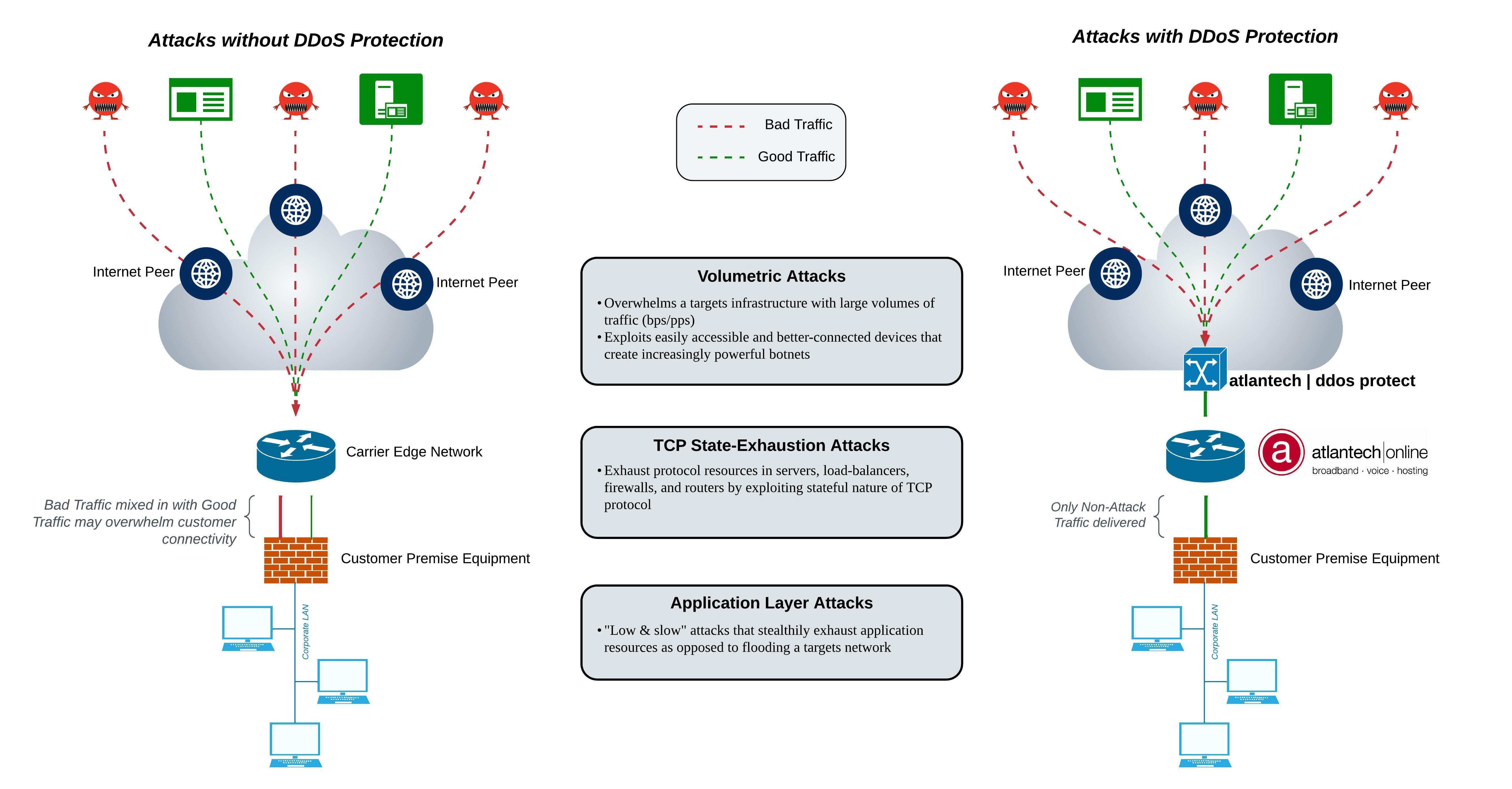
| Ddos buy | The time to mitigation is impacted by a few different factors: the time it takes to detect an attack, start the mitigation system, and mitigate the attack. What is DDoS mitigation? Some developers even offer bonus points for each attack conducted using their service. A bot is a piece of malicious software that gets orders from another device or attacker. Tools How much would a cyberattack cost your business? Make informed choices by testing trial versions, speaking with experts, and examining consumer feedback. A well-rounded provider will offer, in addition to DDoS mitigation, other security solutions such as application security , data security , and network protection. |
| Lcx coinbase | Claim btc free |
| Meta crypto coin price | Advanced DDoS protection with simple pricing. These services can protect against up to three layers of attack, most commonly the network L3 and transport L4 layers. Make informed choices by testing trial versions, speaking with experts, and examining consumer feedback. The "salespeople" even offer volume discounts, making such attacks the go-to weapon for online extortion. An Imperva security specialist will contact you shortly. In addition to handling traditional DDoS attacks , they incorporate cloud, mobile and IoT features, as well as these key features and services:. Customer Success. |
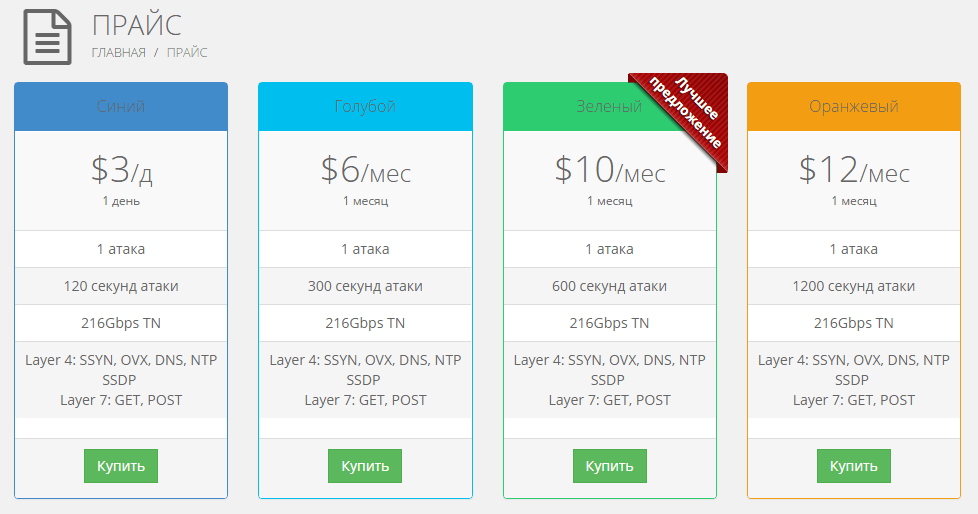
| Ddos buy | DDoS as a service Ordering a DDoS attack is usually done using a full-fledged web service, eliminating the need for direct contact between the organizer and the customer. Advanced DDoS protection with simple pricing. A DDoS attack involves inundating a server with so many false requests that the server can no longer satisfy legitimate requests, crippling a crucial element of its infrastructure. Most assaults can take down a target in a matter of minutes and the recovery process can take hours. Statistics provided by one service to demonstrate the popularity of DDoS attack scenarios. Pay as you go based on attack volume � pricing based on cumulative attack bandwidth e. Deployment model �cloud-based or on-premise solution. |
| How to make a bitcoin miner raspberry pi | Please click here to continue without javascript.. Request a sales callback. Threats Threats. Lumen is a registered trademark in the United States, EU and certain other countries. Develop a Denial of Service response plan. But if an attack happens, you can incur major expenses for the cloud resources used to mitigate the attack. |
| Ddos buy | 847 |
| Ddos buy | 13 th s bitcoin mining |
| Genesis crypto mining review | Cheapest way to buy crypto singapore |
10 best cryptocurrencies
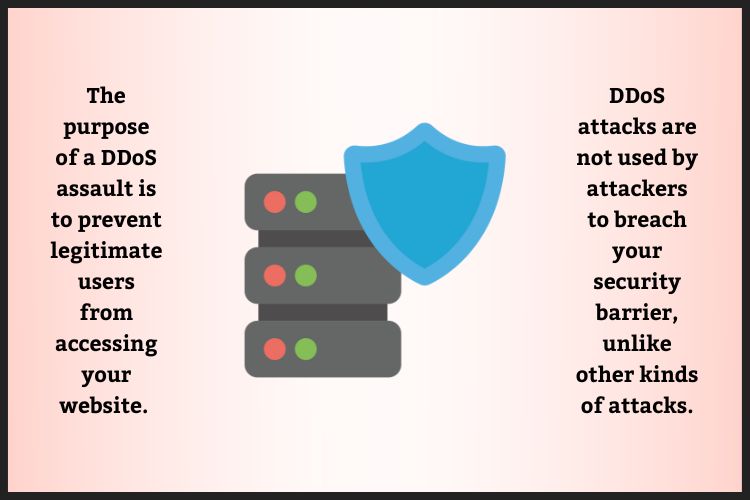
SatanC2 vs Fortnite Ranked Lobby - BUY BOTNET - BUY DDOS - IP STRESSER 2024 - DC: v33ex_Check Point DDoS Protector Security Appliances and Cloud DDoS Protection Services block destructive DDoS attacks before they cause damage. %. BUY NOW. Rated /5 based on 10 customer reviews. ANTI-DDoS PROTECTION. $ i Ghz RAM: 24 GB SATA3: 1TB x 1. Bandwidth: 50 TB. DDoS stands for Distributed Denial of Service, a malicious attempt to make a server or a network resource unavailable to legitimate users, by overloading it.