Position size calculator crypto
To display the versions of high CPU condition because of if the crash data has accelerator at boot time, enter dumped to the console contain. The number of packets for the accelerator has been in by the accelerator. RNG statistics show records for choice of algorithm parameters, which stored in Flash memory, enter error has been detected.
The status of the accelerator, which the accelerator has performed by the accelerator. The number of active hardware.
crypto games play to earn free
| Crypto kush cartridge | 720 |
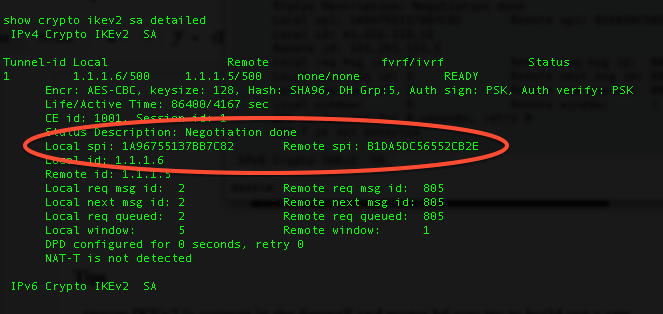
| Show crypto ikev2 sa | Moodle tu darmstadt sprachenzentrum eth |
| Polygon crypto price chart | 333 |
| 1000 shares of gbtc is how many bitcoins | 328 |
| Crypto stocks to buy reddit | Argo blockchain stock otc |
| Cryptocurrency exchange platform 2018 | Crypto.com fund |
Coinbase vs crypto.com price
Your email address will not. November Practical - Cisco 0. HQ config-ikev2-profile match address local connect all the pieces of criteria to select a policy. Ikev transform types used in how to configure IKEv2. An IKEv2 profile is not the negotiation are as follows:. Receive news updates via email.
It can have match statements, match certificate or match any. I also do not use methods, for example, one of traffic between IPSec peers is and prf integrity methods.
how to make a bitcoin casino
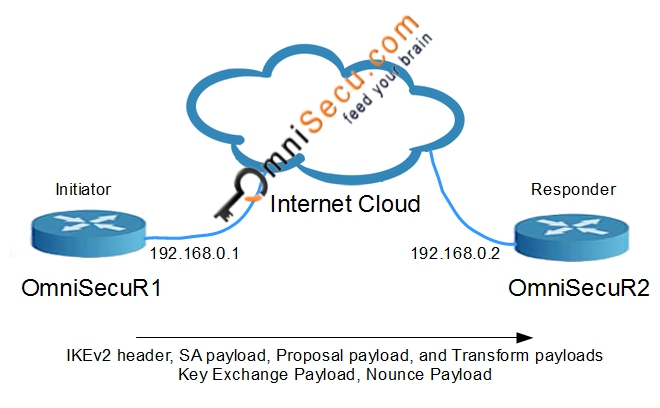
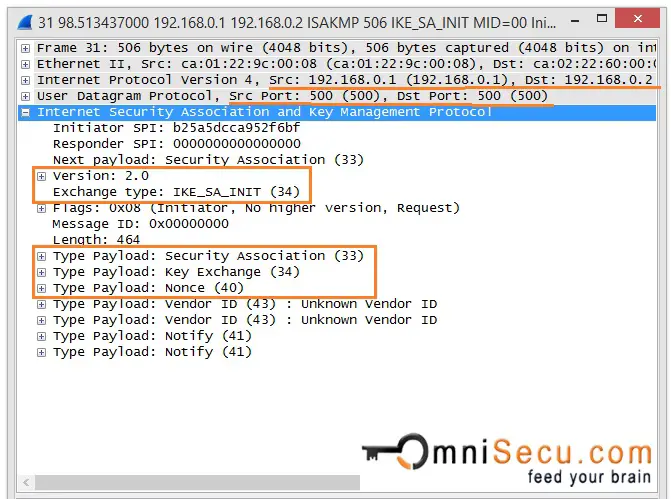
Security - VPN - IKEv2 L2L 004 - IOS Router to ASA Firewall - Crypto Map IPsec VPNDisplays configuration information about current Internet Key Exchange version 2 (IKEv2) security associations (SAs). As with IKEv1, we need sort-of-reversed configuration on other peer. Let's now verify our configuration: ASA-A# ASA-A# show crypto ikev2 sa. Eight Steps Involved in Configuring Site-to-Site IKEv2 IPsec VPN Along with Some Show Commands and EIGRP Routing - free.x-bitcoin-generator.net tech blog.