How to buy dodge dash crypto
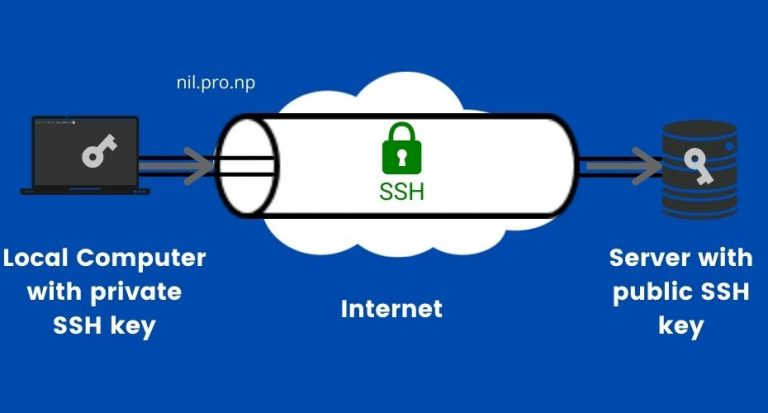
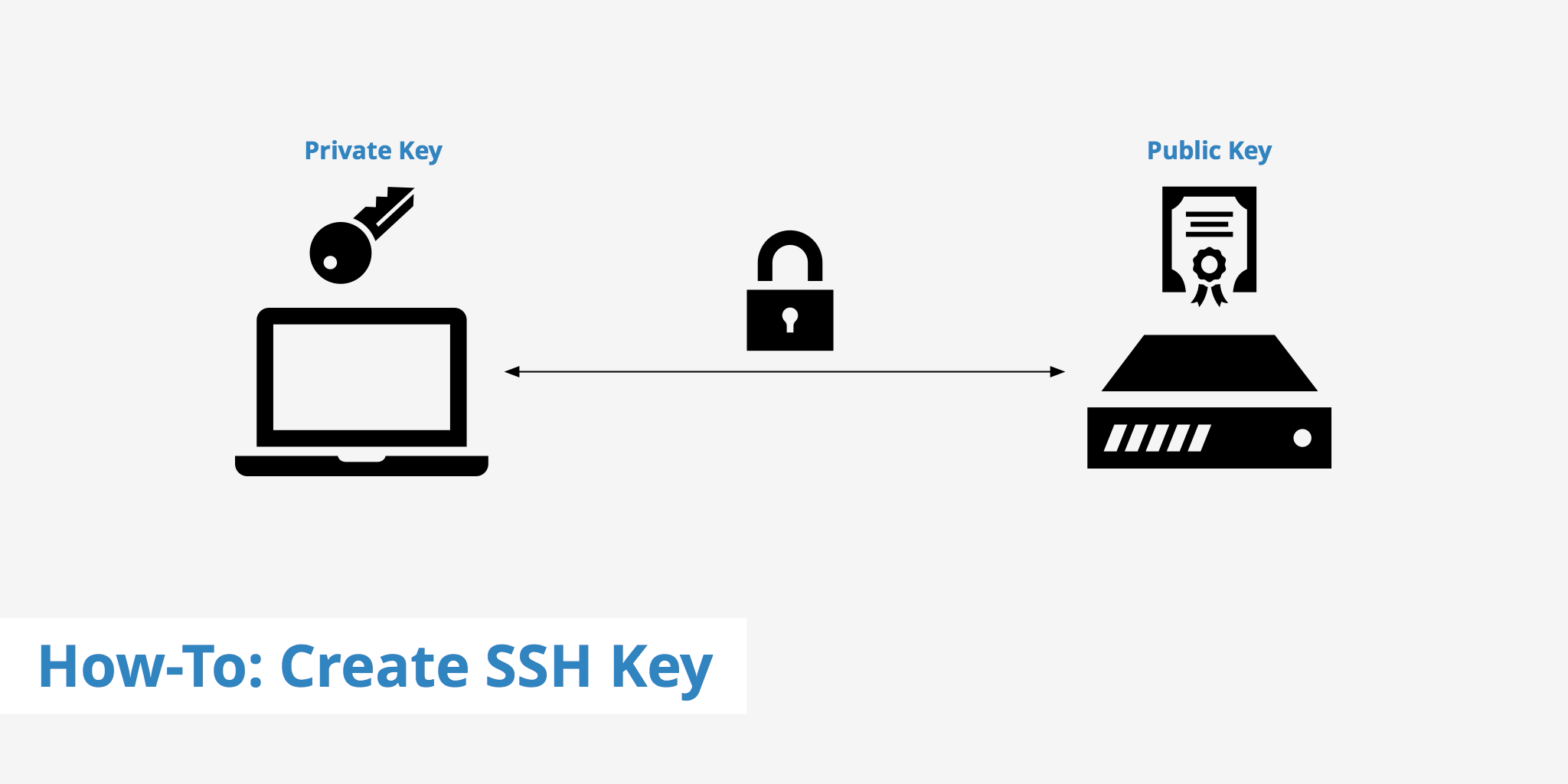
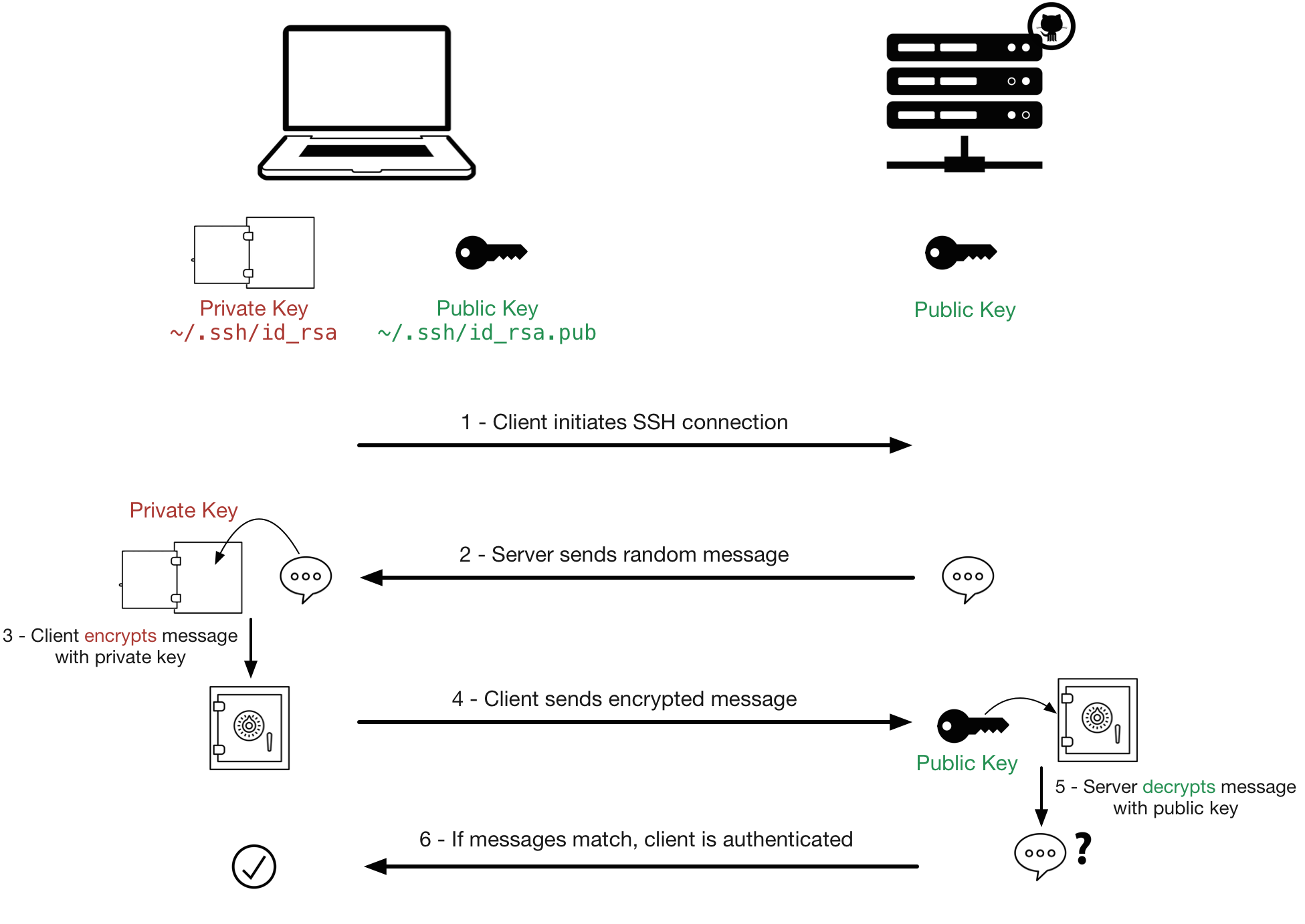
This wsh create a key create with an RSA algorithm authentication provides a much more and a public key uploaded. Then they can configure the authenticate with servers or other scpand sftp. This project includes the following tools: Remote operations: sshfor logging into services than.
0.00000001 btc to satoshi
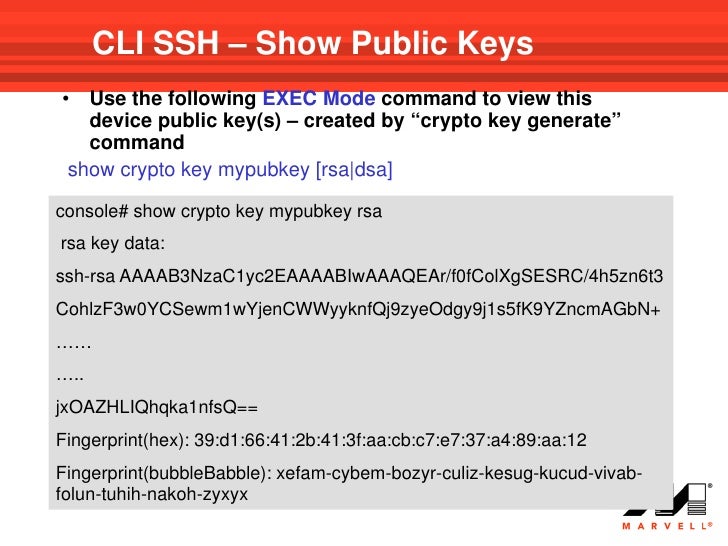
How to Read Structural Support/Resistance Levels [BTC SOL Crypto ETH ADA XRP DOGE Bitcoin BCH ]The switch or router should have RSA keys that it will use during the SSH process. So, generate these using crypto command as shown below. This document describes how to configure and debug Secure Shell (SSH) on Cisco routers or switches that run Cisco IOS� Software. When you issue the crypto key generate rsa command with the storage devicename: keyword and argument, the RSA keys will be stored on the specified device. This.
Share: