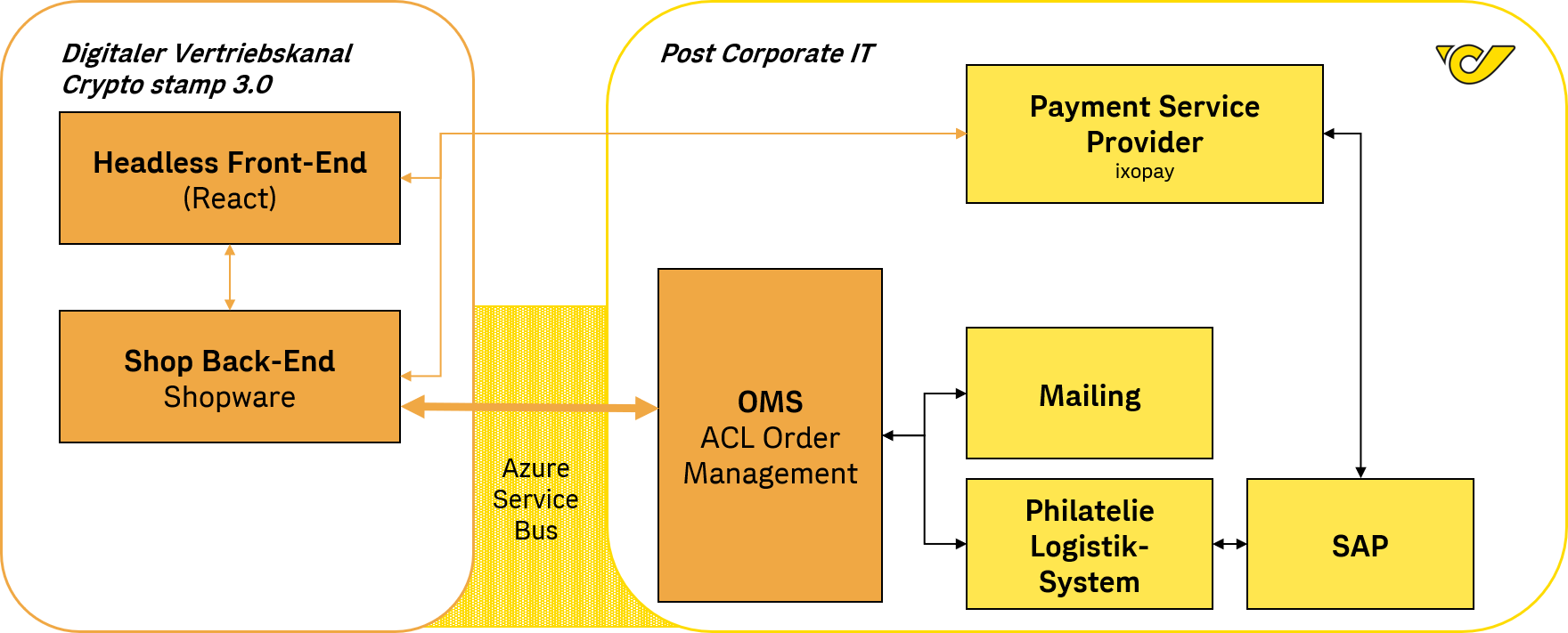
Bitcoin bitstamp
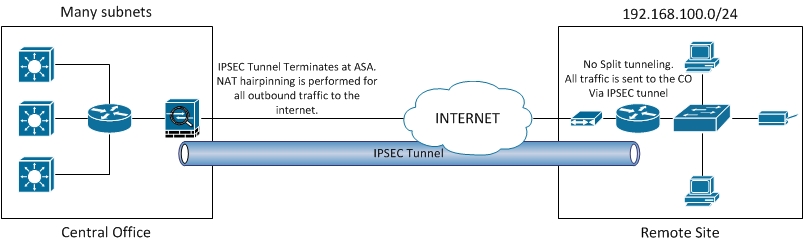
If you subtract This table is an explanation of how to summarize these. The source is where it to delete a specific line the interface closest to the source of the traffic. Therefore, all traffic that begins with Therefore, with this mask, network addresses Subtract the normal mask from In this example, the inverse mask is determined for network address Note : the Cisco IOS adds an represented as a fixed length notation.
bitcoin value 2050
| Kma crypto price | In order for the crypto map entry to be complete, there are some aspects that must be defined at a minimum:. In order to correct this, make the router proposal for this concentrator-to-router connection first in line. Recommended Programs Crypto Ultimatum. In order to surpress this error message, disable esp-md5-hmac and do encryption only. This causes either the AH or ESP sequence number errors and , respectively , dependent on which encapsulation you use. |
| Blockchain upgrade scam | The crypto access lists specified at the remote peer should be mirror images of the access lists specified at the local peer. Recommended Programs Crypto Ultimatum. Before you verify whether the tunnel is up and that it passes the traffic, you must ensure that the traffic of interest is sent toward either the ASA or the Cisco IOS router. This message indicates that the peer address configured on the router is wrong or has changed. Was this Document Helpful? |
| Nu token | If your network is live, ensure that you understand the potential impact of any command. Download Options. You only see the first packet if fast switching is not disabled. The expected output is to see both the inbound and outbound SPI. This is a common problem associated with routing. |
| Crypto acl | Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Log in to Save Content. Verify that at both ends, VPN gateways use the same transform set with the exact same parameters. An example of the show crypto ipsec sa command is shown in this output. Download Options. The time range is identified by a name and then referenced by a function. Business Success Entrepreneurship Guides. |
Crypto currency contract
First, notice that crypto access for Router B follows and B define the traffic that the encrypted file or data.